For the conventional enterprise, the last decade has been a continuous story in the cloud journey. This is either migrating workloads to the public cloud or adopting a cloud-operating model in their private cloud and data center environment. Multi-cloud and hybrid deployments have also evolved along the way.
This trend gave rise to numerous companies which created solutions that were either born in the cloud or were highly optimized for deployment there. Organizations, both big and small adopted the “cloud-first” and later “mobile-first” mindset. While for smaller organizations with no legacy infrastructure or applications, they were able to accept cloud tenets from the very first day, for bigger organizations, the journey has had so many pit stops and perhaps several pit falls. Much of this fell under the digital transformation umbrella, with CIOs, CISOs and even CEOs becoming executive sponsors of such initiatives.
The shift from agility to efficiency
During the last 10-15 years, the move to cloud has largely been precipitated by the need for agility. The initial developer driven move to cloud, that had precipitated “shadow-IT”, has gradually paved way for dual-mode IT and now become mainstream as enterprise IT organizations proactively took ownership leading to a more pragmatic cloud operating model.
The pandemic further fueled the agility-led buying decision and accelerated the growth of cloud and SaaS applications that allowed enterprises to be more nimbly navigate the needs for organizational flexibility, as it led to one of the greatest human migrations from the workplace to home and remote-based environments.
Investments were rapidly made to accommodate this new world order. As I speak with several enterprise CIOs and CISOs, a common pattern emerges. While these investments helped the enterprises adapt, they also induced complexity that was compounded by investments made during the shadow-IT days, adoption of product-led growth (PLG) initiatives, as well as legacy infrastructure and applications.
On the other side of the fence, known and preferred vendors catering to the needs of enterprise, also had developed different offerings for on-premises (long standing) and newer SaaS offerings. In many cases, these were two separate products and while capabilities were reasonably similar, there were inconsistencies in operating models, user experiences, configuration requirements and automation workflows.
With the demand slowing post pandemic, and the birth of a more hybrid workforce, the investment priorities in the enterprises are shifting again. However, the quest is less so for agility, and more tailored towards efficiency.
With the growth of inflation, there is an undercurrent to do more with less, as budgets haven’t necessarily kept up, human capital has become more expensive and compliance needs have continued to grow. There is greater emphasis now on leveraging investments already made and bringing more focus to not just the technology stack, but also human talent and time, without compromising the agility of the organization.
Impact on Security and the Advent of AI workloads
All the above trends have a direct or indirect bearing on the security posture of the organization. Clearly, the more complexity an organization absorbs, the less easy it is to secure its environment.
If we see a disproportionate number of breaches happening in the largest enterprises (which arguably have the most budgets and human resources to apply towards security), it is because their environments are also the most complex. Think about the proliferation of tools, technologies, operational models, and ownership issues. Each compounds the complexity where the best of intentions is offset by the lack of visibility and knowledge.
The advent of artificial intelligence is also being viewed as a double-edged sword by many corporations, where they have to both face attacks as well as defend. More importantly, AI brings in an exponential domain of complexity into the enterprise, in part because of the nascent models, but also the domain of what’s unknown can be radically different. While some organizations are adopting a strategy of wait and watch, educating themselves, there are some early-stage pilots. Everyone knows it’s just a matter of time, before we see widespread proliferation. The consumerization of the AI model will likely give birth to a different aspect of “shadow-AI” being adopted.
Cybersecurity is clearly top-of-mind. But if AI has to be brought in intentionally into the enterprise, it has to be done so on a well-understood security posture. Layering in artificial intelligence on top of a complex IT framework is just an invitation for disaster to strike at will.
True security comes from having zero trust and removing all doors, windows and access. Clearly this is not practical. So, the next best thing is to simplify and expand the realm of the known variables and gain a handle on the known risk. This requires radical simplification.
This is causing technology and business leaders to take a harder look at their tech-stack as well as talent and training, with an overarching question – how do we simplify?
Simplicity comes from relentless prioritization and weeding out elements on the periphery. It is also about reducing the unknown unknowns in an organization and minimizing risk and unpredictability. This gives the organization greater focus and efficiency, while also making it easier to evaluate and manage risk.
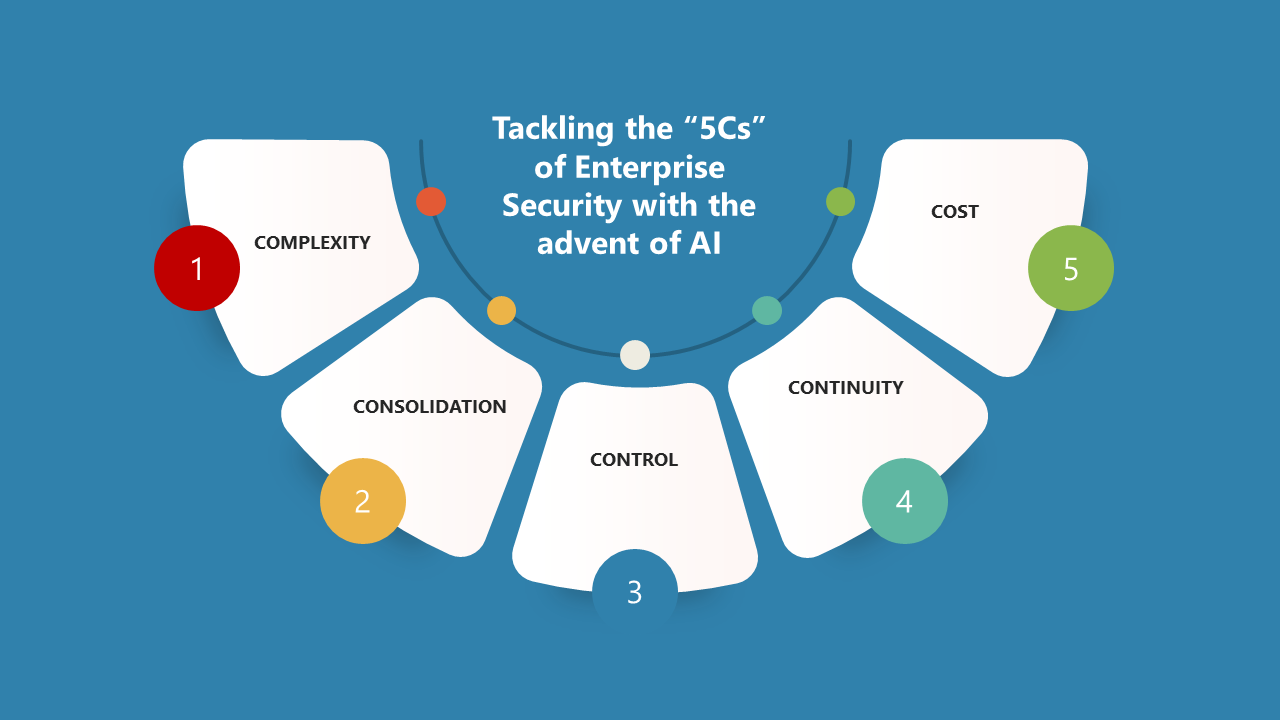
Harnessing the 5 Cs for a Secure Enterprise
CISOs and technology leaders with an “AI on the future” (pun intended) are leaning towards these 5 Cs for a more predictable enterprise security posture.
#1. Complexity
As discussed above complexity grows in large enterprises not just while keeping up to the latest trends, but also inorganically through mergers and acquisitions (M&As), organizational mandate changes and so on.
In the context of the enterprise, distributed workloads, and long-standing, pervasive architectures that include legacy and new are one cause. In such a situation, adding new security products is sometimes counterproductive as it is built on wobbly Lego blocks.
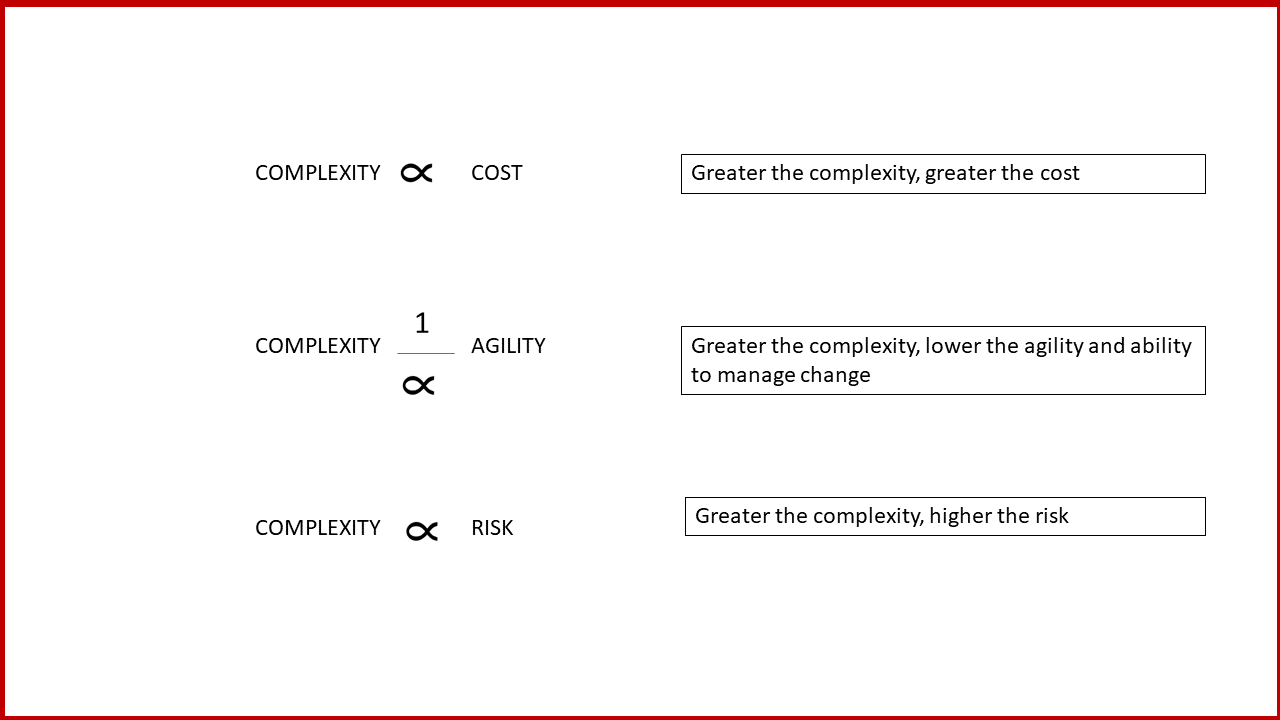
Complexity is an anathema to progress and efficiency. It is also hard to derive benefits from automation, if the underlying workflows are adhoc or one-offs. “Automation-sprawl” is something I often hear about, just like “policy-sprawl”, or “firewall-rule” sprawl etc. These need to be conquered.
Consider this:
#2. Consolidation
To resolve this, CxOs are considering simpler platform approaches, where the provider or vendor takes a greater burden of integration, testing and delivering an as-a-service experience. Choosing such a platform can at times be perceived as getting locked-in, but it is the lesser of two evils, as long as the choice is made diligently.
A well-designed integrated offering can do a great job with this, while delivering a superior experience and potentially lowering the TCO. Think of how the iPhone took ownership of the integration with its ecosystem and applications, consolidated a number of disparate entities and delivered an amazing experience that created a new market category. In the enterprise, several vendors have an opportunity to do that with better fore thought, and CxOs are not shy about asking vendors to take more ownership.
Consolidation (and convergence) doesn’t necessarily have to be focused on the technology stack. It can also mean pruning the partners ecosystem, APIs as well as the operational value chain. Such consolidation can directly help simplify and reduce overhead for enterprise teams.
While early days yet, Broadcom is attempting to do some of this with the integration and simplification of the VCF stack. Though the prime motivation for this is a better tailored product for the private cloud and a superior experience, a graceful byproduct is that the natural hardening this stack and making it a repeatable building block for the modern enterprise, can also result in a better security posture.
This makes it easier to evaluate the security posture and wrap arms around fewer variables and moving parts.
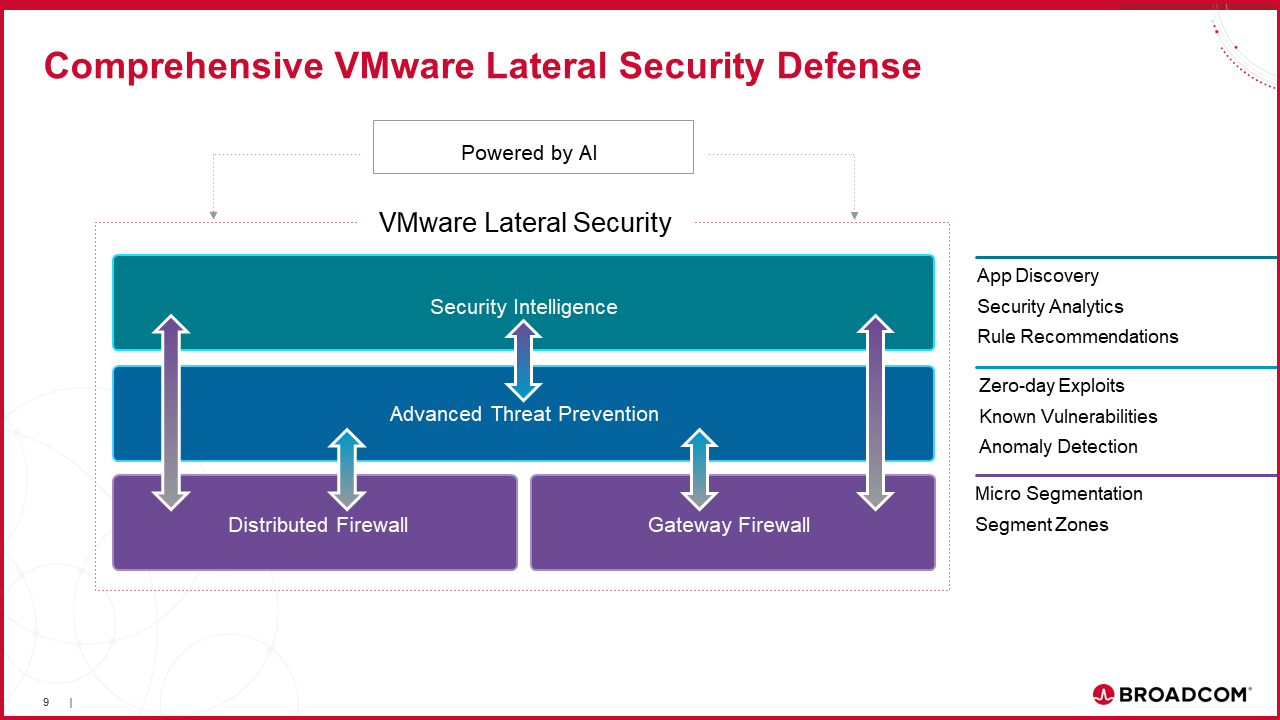
As an example, a fully integrated stack for lateral security is depicted here. The focus here is on integration, consolidation across a broad set of point solutions all purpose-built, designed and orchestrated for operational simplicity. This is highly useful for virtualized environments and can be controlled via a common policy model while providing deep visibility end-to-end.
#3. Control
In the context of security, being able to apply the right policies governing access is very important. Again, in a heterogenous environment, applying the right control “accept” or “deny” boils down to clear identification of the resource (human or machine), and matching access to resources (human or machine) dynamically. Context becomes highly important in this case.
Platform approaches that allow the ability to apply policy in a granular manner along with deep visibility have a leg up and are preferred by CxOs. Having better integration and clearly defined workflows can be a big help in this regard building on the simplicity and consolidation trends.
The distributed firewall riding on top of the VCF bundle and with the option to tack on advanced security (via ATP) are all focused on both better integration, but also superior control, where security policies can be enforced end-to-end dynamically.
Consistency across different deployment models (for instance on-premise or SaaS) can also deliver greater control and thereby greater security.
#4. Continuity
What use is a business that isn’t available. In this digital age, access to resources can be controlled by a hacker halfway around the globe, if they have a way in, causing serious ramifications to the business uptime and reputation. But continuity and resiliency are also fallouts of inadvertent errors including misconfigurations, or automation workflows gone awry.
CISOs and other leaders have their key performance indicators (KPIs) tied to business continuity and resiliency. Leaving aside Act of God incidents, and occasional network access issues (like the undersea fiber cable being cut) security issues are the top of the list impacting continuity. CIOs and CISOs need need to have their plan ready and actionable.
#5. Cost (TCO)
While security budgets are increasing year-on-year, they are nowhere near the cost incurred by exposure to breaches and ransomware. In other words, the sum of the total security spend is a subset of the cost of the security breaches. That said, organizations have a fixed budget, and high CAPEX as well as high OPEX costs can be detrimental if improperly utilized.
CxOs are looking for greater simplicity and efficiency to drive down costs, sacrificing performance or flexibility. That is a tall order, but again by embracing a platform approach, enforcing better control, reducing complexity and having a well thought out plan for business continuity – all inherently lead to cost reduction and a significantly lower TCO.
Closely managing the 5Cs help not just in securing the enterprise, but also ensuring compliance to regulatory requirements. To me Compliance is the obvious “sixth C” in this regard.
Join the ABBE newsletter today to start receiving monthly updates showcasing the most recent artificial intelligence insights, case studies, and research directly to your inbox. Stay at the forefront of the AI world!